Jul 17, 2020 Windows Security is a built-in app available on Windows 10 that provides a user-friendly interface and tools to manage common security features. For example, the experience includes the Microsoft. Windows Security is a built-in app available on Windows 10 that provides a user-friendly interface and tools to manage common security features. For example, the experience includes the Microsoft.
However, Windows Security is pre-installed and ready for you to use at any time. If you want to use Windows Security, uninstall all of your other antivirus programs and Windows Security will automatically turn on. You may be asked to restart your device.
-->The Security Events connector lets you stream all security events from your Windows systems (servers and workstations, physical and virtual) to your Azure Sentinel workspace. This enables you to view Windows security events in your dashboards, to use them in creating custom alerts, and to rely on them to improve your investigations, giving you more insight into your organization's network and expanding your security operations capabilities. You can select which events to stream from among the following sets:
All events - All Windows security and AppLocker events.
Common - A standard set of events for auditing purposes. A full user audit trail is included in this set. For example, it contains both user sign-in and user sign-out events (event IDs 4624, 4634). There are also auditing actions such as security group changes, key domain controller Kerberos operations, and other types of events in line with accepted best practices.
The Common event set may contain some types of events that aren't so common. This is because the main point of the Common set is to reduce the volume of events to a more manageable level, while still maintaining full audit trail capability.
Minimal - A small set of events that might indicate potential threats. This set does not contain a full audit trail. It covers only events that might indicate a successful breach, and other important events that have very low rates of occurrence. For example, it contains successful and failed user logons (event IDs 4624, 4625), but it doesn't contain sign-out information (4634) which, while important for auditing, is not meaningful for breach detection and has relatively high volume. Most of the data volume of this set is comprised of sign-in events and process creation events (event ID 4688).
None - No security or AppLocker events. (This setting is used to disable the connector.)
The following list provides a complete breakdown of the Security and App Locker event IDs for each set:
Event set Collected event IDs Minimal 1102, 4624, 4625, 4657, 4663, 4688, 4700, 4702, 4719, 4720, 4722, 4723, 4724, 4727, 4728, 4732, 4735, 4737, 4739, 4740, 4754, 4755, 4756, 4767, 4799, 4825, 4946, 4948, 4956, 5024, 5033, 8001, 8002, 8003, 8004, 8005, 8006, 8007, 8222 Common 1, 299, 300, 324, 340, 403, 404, 410, 411, 412, 413, 431, 500, 501, 1100, 1102, 1107, 1108, 4608, 4610, 4611, 4614, 4622, 4624, 4625, 4634, 4647, 4648, 4649, 4657, 4661, 4662, 4663, 4665, 4666, 4667, 4688, 4670, 4672, 4673, 4674, 4675, 4689, 4697, 4700, 4702, 4704, 4705, 4716, 4717, 4718, 4719, 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4733, 4732, 4735, 4737, 4738, 4739, 4740, 4742, 4744, 4745, 4746, 4750, 4751, 4752, 4754, 4755, 4756, 4757, 4760, 4761, 4762, 4764, 4767, 4768, 4771, 4774, 4778, 4779, 4781, 4793, 4797, 4798, 4799, 4800, 4801, 4802, 4803, 4825, 4826, 4870, 4886, 4887, 4888, 4893, 4898, 4902, 4904, 4905, 4907, 4931, 4932, 4933, 4946, 4948, 4956, 4985, 5024, 5033, 5059, 5136, 5137, 5140, 5145, 5632, 6144, 6145, 6272, 6273, 6278, 6416, 6423, 6424, 8001, 8002, 8003, 8004, 8005, 8006, 8007, 8222, 26401, 30004
Note
Security Events collection within the context of a single workspace can be configured from either Azure Security Center or Azure Sentinel, but not both. If you are onboarding Azure Sentinel in a workspace that is already getting Azure Defender alerts from Azure Security Center, and is set to collect Security Events, you have two options:
Leave the Security Events collection in Azure Security Center as is. You will be able to query and analyze these events in Azure Sentinel as well as in Azure Defender. You will not, however, be able to monitor the connector's connectivity status or change its configuration in Azure Sentinel. If this is important to you, consider the second option.
Disable Security Events collection in Azure Security Center, and only then add the Security Events connector in Azure Sentinel. As with the first option, you will be able to query and analyze events in both Azure Sentinel and Azure Defender/ASC, but you will now be able to monitor the connector's connectivity status or change its configuration in - and only in - Azure Sentinel.
Set up the Windows Security Events connector
To collect your Windows security events in Azure Sentinel:
From the Azure Sentinel navigation menu, select Data connectors. From the list of connectors, click on Security Events, and then on the Open connector page button on the lower right. Then follow the on-screen instructions under the Instructions tab, as described through the rest of this section.
Verify that you have the appropriate permissions as described under Prerequisites.
Download and install the Log Analytics agent (also known as the Microsoft Monitoring Agent or MMA) on the machines for which you want to stream security events into Azure Sentinel.
For Azure Virtual Machines:
- Click on Install agent on Azure Windows Virtual Machine, and then on the link that appears below.
- For each virtual machine that you want to connect, click on its name in the list that appears on the right, and then click Connect.
For non-Azure Windows machines (physical, virtual on-prem, or virtual in another cloud):
- Click on Install agent on non-Azure Windows Machine, and then on the link that appears below.
- Click on the appropriate download links that appear on the right, under Windows Computers.
- Using the downloaded executable file, install the agent on the Windows systems of your choice, and configure it using the Workspace ID and Keys that appear below the download links mentioned above.
Note
To allow Windows systems without the necessary internet connectivity to still stream events to Azure Sentinel, download and install the OMS Gateway on a separate machine, using the link on the lower right, to act as a proxy. You will still need to install the Log Analytics agent on each Windows system whose events you want to collect.
For more information on this scenario, see the Log Analytics gateway documentation.
For additional installation options and further details, see the Log Analytics agent documentation.
Select which event set (All, Common, or Minimal) you want to stream.
Click Update.
To use the relevant schema in Log Analytics for Windows security events, type
SecurityEventin the query window.
Validate connectivity
It may take around 20 minutes until your logs start to appear in Log Analytics.
Configure the Security events connector for anomalous RDP login detection
Important
Anomalous RDP login detection is currently in public preview.This feature is provided without a service level agreement, and it's not recommended for production workloads.For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Azure Sentinel can apply machine learning (ML) to Security events data to identify anomalous Remote Desktop Protocol (RDP) login activity. Scenarios include:
Unusual IP - the IP address has rarely or never been observed in the last 30 days
Unusual geo-location - the IP address, city, country, and ASN have rarely or never been observed in the last 30 days
New user Vfl wolfsburg 2021 kitsempty spaces the blog. - a new user logs in from an IP address and geo-location, both or either of which were not expected to be seen based on data from the 30 days prior.
Configuration instructions
You must be collecting RDP login data (Event ID 4624) through the Security events data connector. Make sure you have selected an event set besides 'None' to stream into Azure Sentinel.
From the Azure Sentinel portal, click Analytics, and then click the Rule templates tab. Choose the (Preview) Anomalous RDP Login Detection rule, and move the Status slider to Enabled.
Note
As the machine learning algorithm requires 30 days' worth of data to build a baseline profile of user behavior, you must allow 30 days of Security events data to be collected before any incidents can be detected.

Next steps
In this document, you learned how to connect Windows security events to Azure Sentinel. To learn more about Azure Sentinel, see the following articles:
- Learn how to get visibility into your data, and potential threats.
- Get started detecting threats with Azure Sentinel, using built-in or custom rules.
Windows 10 includes Windows Security, which provides the latest antivirus protection. Your device will be actively protected from the moment you start Windows 10. Windows Security continually scans for malware (malicious software), viruses, and security threats. In addition to this real-time protection, updates are downloaded automatically to help keep your device safe and protect it from threats.
Windows 10 in S mode
Some features will be a little different if you're running Windows 10 in S mode. Because this mode is streamlined for tighter security, the Virus & threat protection area has fewer options. But don't worry—the built-in security of this mode automatically prevents viruses and other threats from running on your device, and you'll receive security updates automatically. For more info, see Windows 10 in S mode FAQ.
Important security info
Windows Security is built-in to Windows 10 and includes an antirvirus program called Microsoft Defender Antivirus. (In previous versions of Windows 10, Windows Security is called Windows Defender Security Center).
If you have another antivirus app installed and turned on, Microsoft Defender Antivirus will turn off automatically. If you uninstall the other app, Microsoft Defender Antivirus will turn back on automatically.
If you're having problems receiving Windows Security updates, see Fix Windows Update errors and the Windows Update FAQ.
For info on how to uninstall an app, see Repair or remove an app in Windows 10.
To change your user account to an admin account, see Create a local user or administrator account in Windows 10.
Understand and customize Windows Security features
Windows Security is your home to manage the tools that protect your device and your data:
Microsoft Windows Security
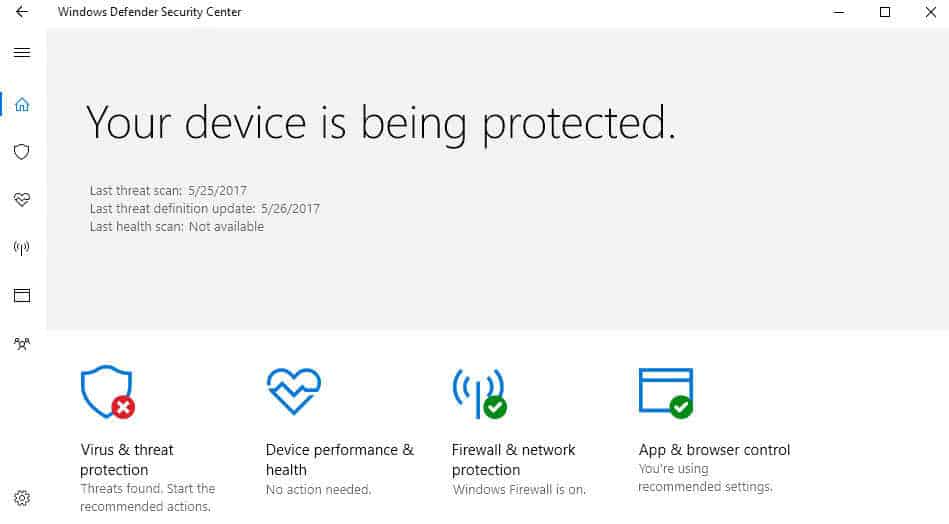
Virus & threat protection. Monitor threats to your device, run scans, and get updates to help detect the latest threats. (Some of these options are unavailable if you're running Windows 10 in S mode.)
Account protection. Access sign-in options and account settings, including Windows Hello and dynamic lock.
Firewall & network protection. Manage firewall settings and monitor what's happening with your networks and internet connections.
App & browser control. Update settings for Microsoft Defender SmartScreen to help protect your device against potentially dangerous apps, files, sites, and downloads. You'll have exploit protection and you can customize protection settings for your devices.
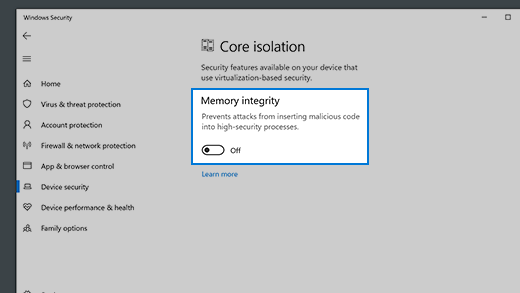
Device security. Review built-in security options to help protect your device from attacks by malicious software.
Promises, Promises (Musical) Sean Hayes, Kristin Chenoweth,Tony Goldwyn, Katie Finneran - Broadway's 2010 Season Revival. 7: Promises, Promises January 2, 1988. Connie makes a resolution to be more patient no matter what, which turns out to be far more difficult than she imagined. The 7 Promises Of God to Man. We are all accustomed to promises. We are also accustomed to seeing them made and broken. Anyone who has lived for a number of years would certainly never lay claim to having kept every promise made. There are many reasons why this is true. To a Babylonian emigrant, 75 years old and childless, owning nothing but his tents and animals, the promises sounded wonderful. In fact, they sounded impossible. Yet, because God himself was making the promise, Abraham 'believed the LORD, and he credited it to him as righteousness' (Genesis 15:6). 7 promises of god printable. Naked Eyes - Promises Promises (U.S. 7 remix) Lyrics. Never had a doubt in the beginning Never a doubt Trusted you true in the beginning I loved you right through On and on we laughed like kids.
Device performance & health. View status info about your device's performance health, and keep your device clean and up to date with the latest version of Windows 10.
Family options. Keep track of your kids' online activity and the devices in your household.
You can customize how your device is protected with these Windows Security features. To access them, select Start > Settings > Update & Security > Windows Security . Then select the feature you want to explore.
Open Windows Security settings

Status icons indicate your level of safety:
Green means your device is sufficiently protected and there aren't any recommended actions.
Yellow means there is a safety recommendation for you.
Red is a warning that something needs your immediate attention.
Run a malware scan manually
When you're concerned about risks to a specific file or folder, you can right-click the file or folder in File Explorer, then select Scan with Microsoft Defender.
If you suspect there's malware or a virus on your device, you should immediately run a quick scan. This is much faster than running a full scan on all your files and folders.
Run a quick scan in Windows Security
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection.
Open Windows Security settingsUnder Current threats, select Quick scan (or in previous versions of Windows 10, under Threat history, select Scan now).
If the scan doesn't find any issues, but you're still concerned, you may want to check your device more thoroughly.
However, Windows Security is pre-installed and ready for you to use at any time. If you want to use Windows Security, uninstall all of your other antivirus programs and Windows Security will automatically turn on. You may be asked to restart your device.
-->The Security Events connector lets you stream all security events from your Windows systems (servers and workstations, physical and virtual) to your Azure Sentinel workspace. This enables you to view Windows security events in your dashboards, to use them in creating custom alerts, and to rely on them to improve your investigations, giving you more insight into your organization's network and expanding your security operations capabilities. You can select which events to stream from among the following sets:
All events - All Windows security and AppLocker events.
Common - A standard set of events for auditing purposes. A full user audit trail is included in this set. For example, it contains both user sign-in and user sign-out events (event IDs 4624, 4634). There are also auditing actions such as security group changes, key domain controller Kerberos operations, and other types of events in line with accepted best practices.
The Common event set may contain some types of events that aren't so common. This is because the main point of the Common set is to reduce the volume of events to a more manageable level, while still maintaining full audit trail capability.
Minimal - A small set of events that might indicate potential threats. This set does not contain a full audit trail. It covers only events that might indicate a successful breach, and other important events that have very low rates of occurrence. For example, it contains successful and failed user logons (event IDs 4624, 4625), but it doesn't contain sign-out information (4634) which, while important for auditing, is not meaningful for breach detection and has relatively high volume. Most of the data volume of this set is comprised of sign-in events and process creation events (event ID 4688).
None - No security or AppLocker events. (This setting is used to disable the connector.)
The following list provides a complete breakdown of the Security and App Locker event IDs for each set:
Event set Collected event IDs Minimal 1102, 4624, 4625, 4657, 4663, 4688, 4700, 4702, 4719, 4720, 4722, 4723, 4724, 4727, 4728, 4732, 4735, 4737, 4739, 4740, 4754, 4755, 4756, 4767, 4799, 4825, 4946, 4948, 4956, 5024, 5033, 8001, 8002, 8003, 8004, 8005, 8006, 8007, 8222 Common 1, 299, 300, 324, 340, 403, 404, 410, 411, 412, 413, 431, 500, 501, 1100, 1102, 1107, 1108, 4608, 4610, 4611, 4614, 4622, 4624, 4625, 4634, 4647, 4648, 4649, 4657, 4661, 4662, 4663, 4665, 4666, 4667, 4688, 4670, 4672, 4673, 4674, 4675, 4689, 4697, 4700, 4702, 4704, 4705, 4716, 4717, 4718, 4719, 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4733, 4732, 4735, 4737, 4738, 4739, 4740, 4742, 4744, 4745, 4746, 4750, 4751, 4752, 4754, 4755, 4756, 4757, 4760, 4761, 4762, 4764, 4767, 4768, 4771, 4774, 4778, 4779, 4781, 4793, 4797, 4798, 4799, 4800, 4801, 4802, 4803, 4825, 4826, 4870, 4886, 4887, 4888, 4893, 4898, 4902, 4904, 4905, 4907, 4931, 4932, 4933, 4946, 4948, 4956, 4985, 5024, 5033, 5059, 5136, 5137, 5140, 5145, 5632, 6144, 6145, 6272, 6273, 6278, 6416, 6423, 6424, 8001, 8002, 8003, 8004, 8005, 8006, 8007, 8222, 26401, 30004
Note
Security Events collection within the context of a single workspace can be configured from either Azure Security Center or Azure Sentinel, but not both. If you are onboarding Azure Sentinel in a workspace that is already getting Azure Defender alerts from Azure Security Center, and is set to collect Security Events, you have two options:
Leave the Security Events collection in Azure Security Center as is. You will be able to query and analyze these events in Azure Sentinel as well as in Azure Defender. You will not, however, be able to monitor the connector's connectivity status or change its configuration in Azure Sentinel. If this is important to you, consider the second option.
Disable Security Events collection in Azure Security Center, and only then add the Security Events connector in Azure Sentinel. As with the first option, you will be able to query and analyze events in both Azure Sentinel and Azure Defender/ASC, but you will now be able to monitor the connector's connectivity status or change its configuration in - and only in - Azure Sentinel.
Set up the Windows Security Events connector
To collect your Windows security events in Azure Sentinel:
From the Azure Sentinel navigation menu, select Data connectors. From the list of connectors, click on Security Events, and then on the Open connector page button on the lower right. Then follow the on-screen instructions under the Instructions tab, as described through the rest of this section.
Verify that you have the appropriate permissions as described under Prerequisites.
Download and install the Log Analytics agent (also known as the Microsoft Monitoring Agent or MMA) on the machines for which you want to stream security events into Azure Sentinel.
For Azure Virtual Machines:
- Click on Install agent on Azure Windows Virtual Machine, and then on the link that appears below.
- For each virtual machine that you want to connect, click on its name in the list that appears on the right, and then click Connect.
For non-Azure Windows machines (physical, virtual on-prem, or virtual in another cloud):
- Click on Install agent on non-Azure Windows Machine, and then on the link that appears below.
- Click on the appropriate download links that appear on the right, under Windows Computers.
- Using the downloaded executable file, install the agent on the Windows systems of your choice, and configure it using the Workspace ID and Keys that appear below the download links mentioned above.
Note
To allow Windows systems without the necessary internet connectivity to still stream events to Azure Sentinel, download and install the OMS Gateway on a separate machine, using the link on the lower right, to act as a proxy. You will still need to install the Log Analytics agent on each Windows system whose events you want to collect.
For more information on this scenario, see the Log Analytics gateway documentation.
For additional installation options and further details, see the Log Analytics agent documentation.
Select which event set (All, Common, or Minimal) you want to stream.
Click Update.
To use the relevant schema in Log Analytics for Windows security events, type
SecurityEventin the query window.
Validate connectivity
It may take around 20 minutes until your logs start to appear in Log Analytics.
Configure the Security events connector for anomalous RDP login detection
Important
Anomalous RDP login detection is currently in public preview.This feature is provided without a service level agreement, and it's not recommended for production workloads.For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Azure Sentinel can apply machine learning (ML) to Security events data to identify anomalous Remote Desktop Protocol (RDP) login activity. Scenarios include:
Unusual IP - the IP address has rarely or never been observed in the last 30 days
Unusual geo-location - the IP address, city, country, and ASN have rarely or never been observed in the last 30 days
New user Vfl wolfsburg 2021 kitsempty spaces the blog. - a new user logs in from an IP address and geo-location, both or either of which were not expected to be seen based on data from the 30 days prior.
Configuration instructions
You must be collecting RDP login data (Event ID 4624) through the Security events data connector. Make sure you have selected an event set besides 'None' to stream into Azure Sentinel.
From the Azure Sentinel portal, click Analytics, and then click the Rule templates tab. Choose the (Preview) Anomalous RDP Login Detection rule, and move the Status slider to Enabled.
Note
As the machine learning algorithm requires 30 days' worth of data to build a baseline profile of user behavior, you must allow 30 days of Security events data to be collected before any incidents can be detected.
Next steps
In this document, you learned how to connect Windows security events to Azure Sentinel. To learn more about Azure Sentinel, see the following articles:
- Learn how to get visibility into your data, and potential threats.
- Get started detecting threats with Azure Sentinel, using built-in or custom rules.
Windows 10 includes Windows Security, which provides the latest antivirus protection. Your device will be actively protected from the moment you start Windows 10. Windows Security continually scans for malware (malicious software), viruses, and security threats. In addition to this real-time protection, updates are downloaded automatically to help keep your device safe and protect it from threats.
Windows 10 in S mode
Some features will be a little different if you're running Windows 10 in S mode. Because this mode is streamlined for tighter security, the Virus & threat protection area has fewer options. But don't worry—the built-in security of this mode automatically prevents viruses and other threats from running on your device, and you'll receive security updates automatically. For more info, see Windows 10 in S mode FAQ.
Important security info
Windows Security is built-in to Windows 10 and includes an antirvirus program called Microsoft Defender Antivirus. (In previous versions of Windows 10, Windows Security is called Windows Defender Security Center).
If you have another antivirus app installed and turned on, Microsoft Defender Antivirus will turn off automatically. If you uninstall the other app, Microsoft Defender Antivirus will turn back on automatically.
If you're having problems receiving Windows Security updates, see Fix Windows Update errors and the Windows Update FAQ.
For info on how to uninstall an app, see Repair or remove an app in Windows 10.
To change your user account to an admin account, see Create a local user or administrator account in Windows 10.
Understand and customize Windows Security features
Windows Security is your home to manage the tools that protect your device and your data:
Microsoft Windows Security
Virus & threat protection. Monitor threats to your device, run scans, and get updates to help detect the latest threats. (Some of these options are unavailable if you're running Windows 10 in S mode.)
Account protection. Access sign-in options and account settings, including Windows Hello and dynamic lock.
Firewall & network protection. Manage firewall settings and monitor what's happening with your networks and internet connections.
App & browser control. Update settings for Microsoft Defender SmartScreen to help protect your device against potentially dangerous apps, files, sites, and downloads. You'll have exploit protection and you can customize protection settings for your devices.
Device security. Review built-in security options to help protect your device from attacks by malicious software.
Promises, Promises (Musical) Sean Hayes, Kristin Chenoweth,Tony Goldwyn, Katie Finneran - Broadway's 2010 Season Revival. 7: Promises, Promises January 2, 1988. Connie makes a resolution to be more patient no matter what, which turns out to be far more difficult than she imagined. The 7 Promises Of God to Man. We are all accustomed to promises. We are also accustomed to seeing them made and broken. Anyone who has lived for a number of years would certainly never lay claim to having kept every promise made. There are many reasons why this is true. To a Babylonian emigrant, 75 years old and childless, owning nothing but his tents and animals, the promises sounded wonderful. In fact, they sounded impossible. Yet, because God himself was making the promise, Abraham 'believed the LORD, and he credited it to him as righteousness' (Genesis 15:6). 7 promises of god printable. Naked Eyes - Promises Promises (U.S. 7 remix) Lyrics. Never had a doubt in the beginning Never a doubt Trusted you true in the beginning I loved you right through On and on we laughed like kids.
Device performance & health. View status info about your device's performance health, and keep your device clean and up to date with the latest version of Windows 10.
Family options. Keep track of your kids' online activity and the devices in your household.
You can customize how your device is protected with these Windows Security features. To access them, select Start > Settings > Update & Security > Windows Security . Then select the feature you want to explore.
Open Windows Security settings
Status icons indicate your level of safety:
Green means your device is sufficiently protected and there aren't any recommended actions.
Yellow means there is a safety recommendation for you.
Red is a warning that something needs your immediate attention.
Run a malware scan manually
When you're concerned about risks to a specific file or folder, you can right-click the file or folder in File Explorer, then select Scan with Microsoft Defender.
If you suspect there's malware or a virus on your device, you should immediately run a quick scan. This is much faster than running a full scan on all your files and folders.
Run a quick scan in Windows Security
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection.
Open Windows Security settingsUnder Current threats, select Quick scan (or in previous versions of Windows 10, under Threat history, select Scan now).
If the scan doesn't find any issues, but you're still concerned, you may want to check your device more thoroughly.
Run an advanced scan in Windows Security
Windows Security Network Credentials
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection.
Under Current threats, select Scan options (or in previous versions of Windows 10, under Threat history, select Run a new advanced scan).
Select one of the scan options:
Full scan (check files and programs currently running on your device)
Custom scan (scan specific files or folders)
Microsoft Defender Offline scan (run this scan if your device has been, or could potentially be, infected by a virus or malware). Learn more about Microsoft Defender Offline
Select Scan now.
Note: Because of streamlined security, this process isn't available if you're running Windows 10 in S mode.
Schedule your own scan
Even though Windows Security is regularly scanning your device to keep it safe, you can also set when and how often the scans occur.
Antivirus
Schedule a scan
Select the Start button, type schedule tasks in the Search box, and in the list of results, select Task Scheduler.
In the left pane, select the arrow (>) next to Task Scheduler Library to expand it, do the same with Microsoft > Windows, and then scroll down and select the Windows Defender folder.
In the top-center pane, select Windows Defender Scheduled Scan. (Point to the choices to see the full names.)
In the Actions pane on the right, scroll down and then select Properties.
In the window that opens, select the Triggers tab, and then select New.
Set your preferred time and frequency, and then select OK.
Review the schedule and select OK.
Windows Security Downloads
Note: Because of streamlined security, this process isn't available if you're running Windows 10 in S mode.
Turn Microsoft Defender Antivirus real-time protection on or off
Sometimes you may need to briefly stop running real-time protection. While real-time protection is off, files you open or download won't be scanned for threats. However, real-time protection will soon turn on automatically again to protect your device.
Turn real-time protection off temporarily
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection > Manage settings. (In previous versions of Windows 10, select Virus & threat protection > Virus & threat protection settings.)
Open Windows Security settingsSwitch the Real-time protection setting to Off and choose Yes to verify.
Note: Because of streamlined security, this process isn't available if you're running Windows 10 in S mode.
